
Facts You Must Know About Data Protection In SAP Using UI Masking And Logging Solution
Facts You Must Know About Data Protection in SAP Using UI Masking and Logging Solution This article will portray what "signifies" improving the framework and information security are accessible in SAP when all is said in done. Present two arrangements explicitly equipped at ensuring information against accessible to secure there are in SAP innovation. It is vital to know a session information security through SAP UI covering and logging arrangements. UI Masking is deterrent control for taking care ofinformation security. It is an active type of covering the presentation of delicate information to hide explicit information except if needed for the undertaking.
Critical Business Needs to Be Tended to By UI Masking and UI Logging.
- Solid control who gets delicate data shown in SAP exchanges and applications.
- Increment insurance of delicate information against robbery and misuse.
- Identify conceivably hazardous admittance to delicate information quickly, and lead a significant investigation to make the correct moves
- Better conform to business or lawful prerequisites.
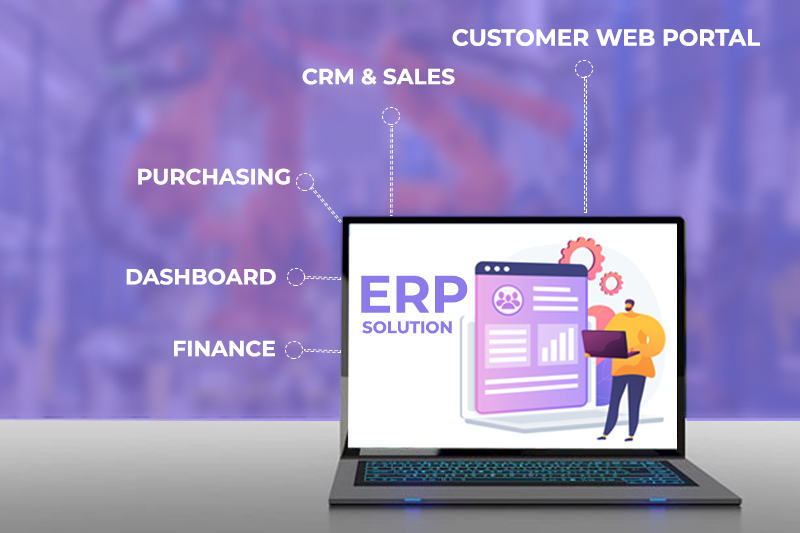
How SAP UI Masking Functions
The SAP UI masking is utilizing to make certain delicate information open just to approved people. If a representative doesn't have the necessary rights, a specific worthis absent in an information outline. This arrangement veils delicate information on theworker in the blink of an eye before it is the yield on the end gadget. Moreover, handling in the SAP UI is obstructed. There is resulting insurance in table presentation, send out situations, download or on paper. When getting to ensured information fields, auditable and archivable access can utilize. For a worker, it may not need to close all compensation slips or bank subtleties.
Log Information Access: How SAP UI Logging Works
With SAP UI logging, admittance to touchy information is unequivocally logged. Theoutcome is an organized and definite information access convention. It empowers an examination of which client has gotten information, how, and in which setting. The logging happens based on trips there and back.
As compare to UI masking, UI logging is a somewhat delicate methodology. Access isn't hindered straightforwardly here but instead followed to determine activity ways or ramifications for information security if fundamental. There are both mechanized controls that ready you for sketchy information access and the alternative of manual controls. Incorporation in SAP ETD is likewise conceivable. The investigation can robotize, and the UI logging can be utilized as an information hotspot for ETD.
Expenses
ExpensesAs a matter of first importance, with other SAP items, the size of the organization andthe number of clients is additionally considered in an expense explanation. The permitcharge must be paid once and incorporates the total, vast, and limitless utilization rights.










Add a comment